Data Analytics
- Home
- Our Services
- Data Analytics
Data Analytics
Data is unlike any other asset your organization owns. It never wears out, it never drains, and it can be used repeatedly. But the value in data is not in having it, it’s in how you use it and unlock its value. Aura Data enables data-driven enterprises by providing teams the power to use data analytics and AI to gain competitive advantages and drive next-level business results.
Aura Data works with industry leading artificial intelligence (AI), analytics, and the Internet of Things (IoT) providing enterprises next-generation, cloud-native enterprise data ecosystem.
The Graph Database Platform for Today’s Intelligent Applications
Powered by native graph technology, Neo4j stores and manages data in its more natural, connected state, maintaining data relationships that deliver lightning-fast queries, deeper context for analytics, and a pain-free modifiable data model.
The Fastest Path to Graph
Neo4j gives developers and data scientists the most trusted and advanced tools to quickly build today’s intelligent applications and machine learning workflows. Available as a fully managed cloud service or self-hosted.
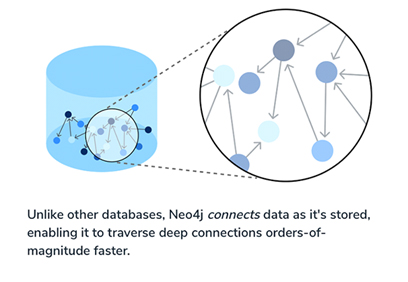
Unlike other databases, Neo4j connects data as it’s stored, enabling it to traverse deep connections orders-of-magnitude faster.
At the core of the Neo4j Graph Data Platform is the Neo4j Graph Database, a native graph data store built from the ground up, to leverage not only data but also data relationships. Unlike other types of databases, Neo4j connects data as it’s stored, enabling queries never before imagined, at speeds never thought possible.
Neo4j Bloom is an easy-to-use graph exploration application for visually interacting with Neo4j graphs. Bloom gives graph novices and experts alike the ability to visually investigate and explore graph data from different business perspectives.
Bloom’s illustrative, codeless search-to-visualization design makes it the ideal interface for fostering communication between peers, managers and executives, and sharing the work of graph development and analytics teams.

IMPORT DATA IN MINUTES
Easy to import data from spreadsheets, cloud or on-premises databases. Gain a holistic view of your business in minutes.
INSTANT DEVELOPMENT
Deploy faster and start analyzing, and share your data with minimal training. Get useful business insights from your data and collaborate in mere minutes.
SCALE UP & DOWN EASILY
Easily scale up or down as your usage expands.To add user licenses to accommodate your future business needs.
SELF SERVICE B I
Gain real-time business insights and solve the problem as they occur or seize opportunities as they arise. With advance Dahboard.
SAFE GUARD YOUR DATA
With strong governance rules of BI software, you can control who can view and has access to sensitive information and who doesn’t.
SHARE INSIGHT EASILY
Break down the silos. Share dashboards and reports to management, senior leaders or anyone in your organization.
DATA VISUALIZATION
Grabs your interest and keep your eyes focused on key messaging. Our business intelligence and analytics platform help you to depict a story in form of stunning, interactive graphs and charts, matrix, scatter plots and heat maps.
ANY TIME ANY WHERE
Access your most important data wherever you are, whenever you need it, on whatever device you have with you. Get updates, proper insights, proper data security, graph,charts,where ever your in this world
USER FRIENDLY
Usability can be described as the capacity of a system to provide a condition for its users to perform the tasks safely, effectively, and efficiently while enjoying the experience.Any individual can use it easily & accessible really userfriendly innovation
We’re not just protecting users, customers, and patients. We’re protecting your business as well.
We know how to separate the signal from the noise. Data, analytics and AI are opening the door to new possibilities for how organizations can grow and differentiate themselves against competition at an accelerated pace. As the C-suite looks for ways to improve utilization and efficiency, unlock new revenue streams and have the ability (and agility) to create new business models, all paths to value share a common denominator… data.
More than half (52%) of the organizations with future-ready operations are already using data and analytics at scale. Reinventing how data and AI initiatives are executed against business strategy results in an organization that can realize a return on investment at speed and ultimately build the case to move from AI pilots to enterprise-wide business transformation.
With Data-driven Reinvention, data at its core becomes the ultimate competitive asset and differentiator, and by scaling AI with cloud, organizations can reposition their offerings, extend capabilities and improve data and AI maturity to create new sources of value and sustainable growth.
Ready to see how Data Analytics can help?
Need a hand with your security program? Let our Data Analytics experts help.
17
of executives felt confident they had the necessary information and insights to make informed business decisions during the pandemic.
76
of executives plan to accelerate digital transformation, including an emphasis on moving to cloud (26% increase compared to pre-covid).
18
revenue growth when digital operating models are used to drive agility at speed.
81
of organizations lack an enterprise data strategy to fully capitalize on their data assets.
Managed Infrastructure and Security Services
While disruptive technologies are a key driver of innovation and efficiency, business priorities change quickly and the customers often struggle to catch up.
IT organizations continually need newer ways to reduce costs and work efficiently while ensuring quality and security. As a result, enterprises are adopting managed infrastructure services and undergoing rapid IT transformations to build business models that adapt to Mobile Computing, Cloud Computing, Big Data, and Social Collaboration.
To eliminate security concerns when adopting new technologies, businesses also rely on infrastructure security services from managed security service provides. But most managed security service providers do not deliver a complete solution that incorporates both infrastructure security services and managed security services.
Happiest Minds Managed Infrastructure Services enable customers to reduce support costs while significantly improving visibility into the performance of the IT infrastructure.
We deliver innovative managed infrastructure services, along with managed security services using both cloud and traditional technologies, combined with collective business, technical and industry expertise.
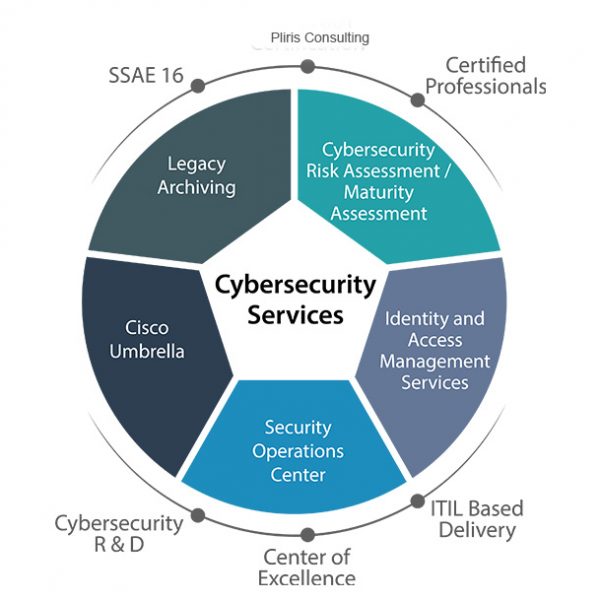
IT Security Services
Today’s threat landscape is dynamic. The proliferation of disruptive technologies like mobile, social, cloud and big data has been increasingly impacting protection strategies. These technologies will continue to add to the complexity and drive the security needs of the IT infrastructure and information assets. They will also challenge integrity of current security controls and will risk enterprise data and intellectual property (IP). Thus, it’s important that businesses have a strategy to deliver effective enterprise security risk management and situational awareness using defense-in-depth strategies, monitoring, analysis and reporting.
At Happiest Minds, we draw on our deep expertise of a large pool of experienced security professionals to offer IT security solutions that address the key challenges faced by enterprises today. Our IT security services aim to improve the agility, flexibility and cost effectiveness of the next generation needs of information security and compliance programs. We ensure a holistic risk driven approach for organizations with our solutions in the areas of identity and access governance, data protection, risk & compliance, threat management and mitigation (application, network & mobile) and cyber security monitoring & management.
Identity and Access Management
Enterprises today, need immediate, easy and secure access to information anytime, anywhere; but with effective measures of control over access and protection from threats. They also have the mandate to abide by several governments and industry specific regulations. With path-breaking advancements in technology such as M2M communication, BYOD, Internet of Things – on one side productivity has grown manifold, on the other, it has exposed organizations to innumerable threats and vulnerabilities both external and internal. Moreover, during a regulatory audit, often organizations opt for manual or semi-automated methods that are prone to errors and could run the risk of a failed audit.
In the face of this constant IT landscape transformation, Identity and Access Management services have become an important part of IT planning and strategy. Businesses need to protect their valuable assets and as threats continue to evolve, Identity and Access Management services also need to be in place to prevent such malicious attacks. With the right Access Management services, IT can authorize access and grant the necessary privileges to both internal and external stakeholders. With Happiest Minds, these obstacles are overcome with an up-to-date platform comprising of effective and reliable Identity and Access Management services.
IT Security Assurance
Timely identification, assessment and management of security risks associated with business applications, networks, mobile devices and related technology environments enable enterprise stakeholders to address emerging threats while maintaining compliance with applicable regulations, legislative requirements and industry standards. Thus, proactive remediation of design flaws and IT security assurance in the business system is important to prevent customer lawsuits, legal penalties, regulatory fines and loss of reputation.
Organizations require best in class technology, robust processes and technical specialists to empower business owners to continuously innovate and focus on the core business without compromising on security. And that’s what makes IT security assurance imperative.